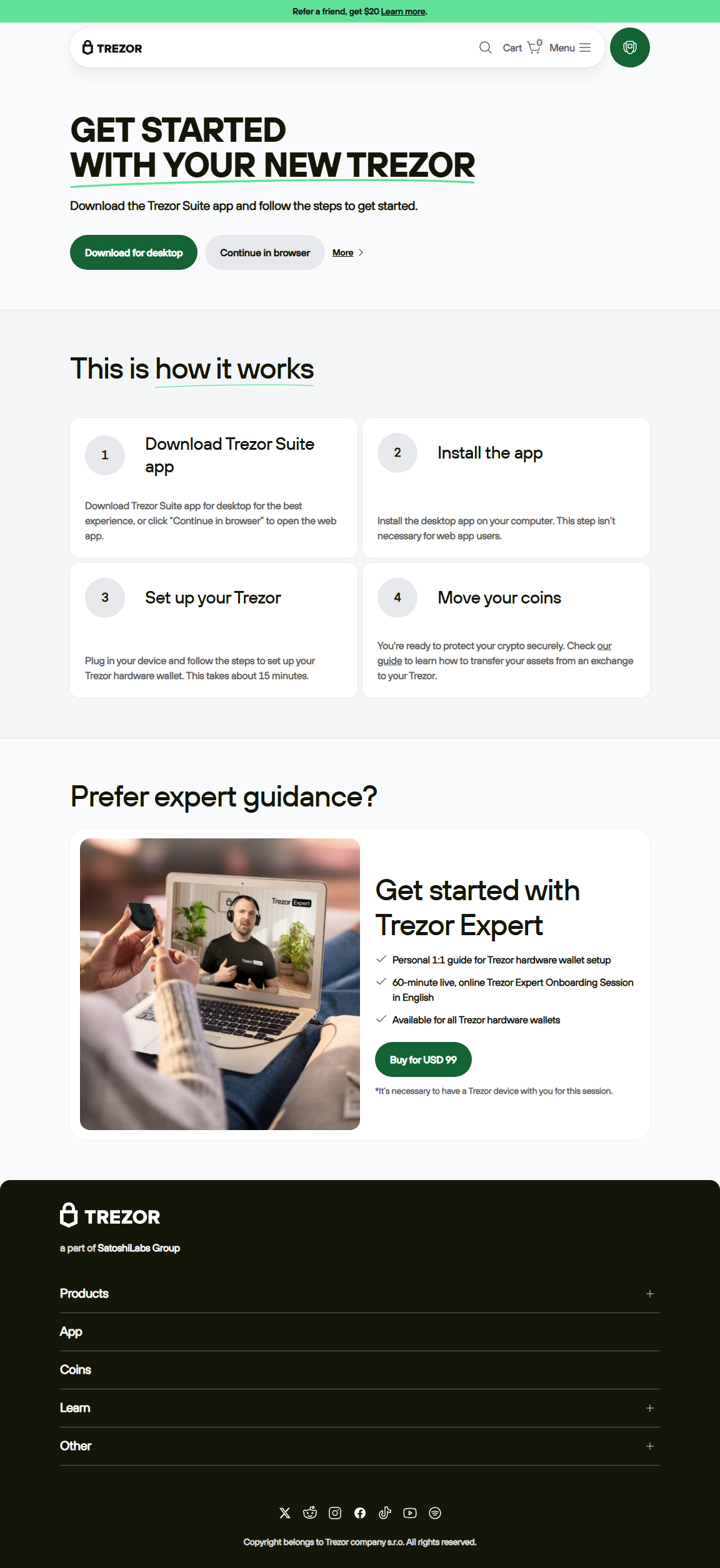
Trezor Login: Secure Access to Your Crypto Wallet
Learn how Trezor Login works and how to securely access your cryptocurrency assets using Trezor Suite.
What is Trezor Login?
Trezor Login is the process of accessing your Trezor hardware wallet through Trezor Suite or other compatible interfaces. This process ensures that your private keys remain securely stored on the device and never exposed to the internet. Trezor Login is designed for both beginners and intermediate users to safely manage, send, receive, and track cryptocurrencies.
Step-by-Step Guide to Trezor Login
Step 1: Install Trezor Suite
Download Trezor Suite from the official Trezor website for your desktop or mobile device. Only download from official sources to avoid phishing scams.
Step 2: Connect Your Trezor Device
Plug in your Trezor hardware wallet via USB. Trezor Suite will detect your device and guide you through initialization or recovery.
Step 3: Authenticate with PIN
Enter your PIN directly on your Trezor device during login. This step ensures that unauthorized users cannot access your wallet, even if your computer is compromised.
Step 4: Access Your Wallet
Once authenticated, Trezor Suite displays your portfolio, balances, and recent transactions. You can now send, receive, and stake cryptocurrencies securely.
Security Features of Trezor Login
- Offline Private Keys: Your keys never leave the device.
- PIN Authentication: Device-level PIN ensures authorized access only.
- Recovery Seed: Offline backup in case the device is lost or damaged.
- Encrypted Communication: Secure USB connection between device and Trezor Suite.
- Firmware Verification: Prevents tampered devices from being used.
Advanced Trezor Login Features for Intermediate Users
- Manage multiple cryptocurrency accounts with real-time portfolio tracking.
- Analyze transaction history with detailed analytics.
- Stake supported coins like Tezos and Tron securely.
- Swap cryptocurrencies directly within Trezor Suite.
- Integrate with DeFi and NFT platforms while keeping keys offline.
Trezor Login vs Other Wallet Access Methods
| Feature | Trezor Login | Ledger Login | Mobile Wallet Apps |
|---|---|---|---|
| Security | Offline keys, PIN protection | Offline keys, PIN protection | Hot wallet, exposed online |
| Ease of Use | Beginner-friendly interface | Beginner-friendly interface | Very easy |
| Portfolio Tracking | Real-time multi-account | Real-time multi-account | Basic tracking |
User Experience: Trezor Login in Action
Priya, a new crypto investor, was unsure how to securely manage multiple assets. By performing Trezor Login with her device, she accessed her portfolio, staked coins, and sent crypto safely. “Trezor Login gave me confidence in managing my digital assets securely,” she shares.
Frequently Asked Questions (FAQs)
1. What is Trezor Login?
Trezor Login is the process of securely accessing your Trezor hardware wallet using Trezor Suite or other compatible apps.
2. Can I log in without a Trezor device?
No. Trezor Login requires a Trezor hardware wallet to keep private keys offline.
3. Is it safe to use Trezor Login on public Wi-Fi?
Yes. Keys remain on the device, minimizing risk. Using a VPN adds extra security.
4. What if I forget my PIN?
If you forget your PIN, use your recovery seed to reset the device and regain access.
Conclusion: Mastering Trezor Login
Trezor Login is essential for safely accessing and managing your cryptocurrency assets. By keeping private keys offline and requiring PIN authentication, it provides top-notch security. Whether you’re a beginner or intermediate user, mastering Trezor Login allows you to track your portfolio, send and receive crypto, stake coins, and integrate with DeFi platforms confidently.